Varonis has released its 2021 Manufacturing Data Risk Report. It which examines the state of data security within industrial manufacturers and engineering firms.
The report found cybersecurity maturity in the manufacturing sector lags behind other industries. That includes finance, with nearly half of all companies still underprepared for a disruptive attack. It is the sensitive and often highly valuable nature of their data which specifically puts manufacturers at risk – this data is overexposed and under protected, and to limit the damage attackers can do, companies must improve their cyber security practices.
Threats against the manufacturing sector continue. From big game ransomware groups that steal victim’s data before encrypting it, to nation-state attackers seeking technology secrets, to company insiders looking for information to grab and sell to the highest bidder. Recent news headlines show how crippling ransomware attacks can halt assembly lines and disrupt supply chains.
Manufacturing was the fifth most targeted industry in 2020, with the average data breach costing $4.99 million. The average breach in the manufacturing sector takes 220 days to contain — one of the longest threat lifecycles out of any industry. Overexposed information — especially sensitive data – exponentially increases risk. This exposure is your “blast radius” — think of it as all the damage an attacker can do once inside your environment. If just one employee clicks on a phishing email, an attacker can potentially access every file an employee can touch.
It examines the state of data security – on-premises, cloud, and hybrid environments – for industrial manufacturers and engineering firms, by analysing a random sample of Data Risk Assessments for 50 companies — and a total of 4 billion files — to determine how data is exposed and at risk.
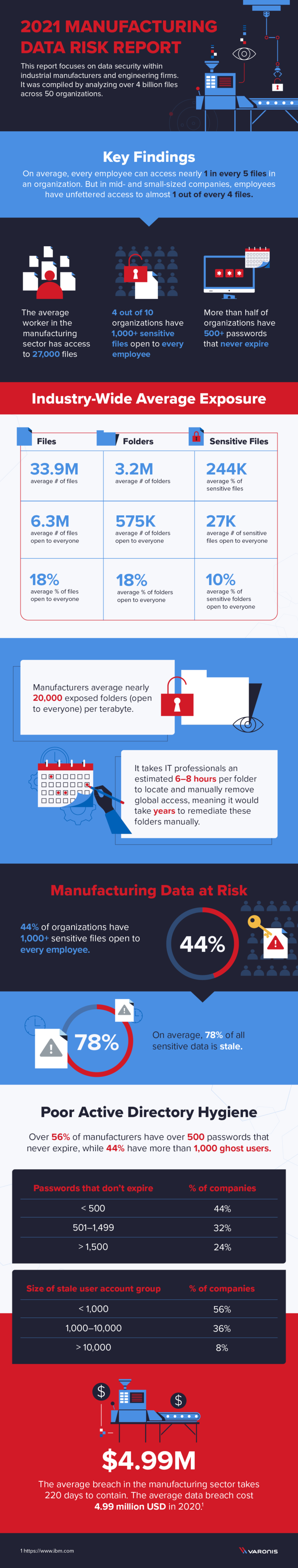
Key report findings include:
- Every employee can access, on average, 6 million files on their first day on the job.
- 4 in 10 organisations have 1,000+ sensitive files open to every employee.
- 44% of companies have more than 1,000 active “ghost user” accounts enabled.
- More than half of companies have 500+ accounts with passwords that never expire.
LARGER COMPANIES ARE 2 x MORE EXPOSED
On average, every employee has access to over 6 million files. That is, nearly one out of every five files, on their first day on the job. For large companies, that number doubles. That is, at firms with more than 1,500 workers, employees can access over 12 million files. One out of every ten files open to everyone in the company is sensitive. These files may include intellectual property, employee data, manufacturing and supply chain information, product development documentation, marketing plans, and more.
PROTECTING MANUFACTURING DATA
Global access groups (e.g., Everyone, Domain Users, Authenticated Users) are helpful for internal collaboration. But they also make it much easier for cybercriminals to infiltrate your environment. If a bad actor compromises one end user, they can gain a foothold that enables them to copy, share, delete and change unprotected sensitive information. 44% of manufacturing companies average 1,000+ files open to every employee. And more than one in five have 10,000 files open to every employee. For these companies with overexposed sensitive data, limiting open access by enforcing a least privilege model is a critical part of risk reduction. Manufacturing companies store above-average amounts of stale sensitive data, which increases their attack surface and inflates storage costs unnecessarily. On average, 78% of an organisation’s sensitive files are stale and could be deleted or archived.
VULNERABILITIES IN ACTIVE DIRECTORY
Inactive user and service accounts that remain enabled long after employees leave (aka. “ghost users”) provide attackers with plenty of time to brute-force their way into your environment and, once inside, move through your data stores. From there, they can quietly steal data and avoid detection before encrypting it. Inactive, but enabled, privileged admin accounts with passwords that never expire are one of the best gifts you can give cybercriminals. These often overlooked vulnerabilities are difficult to detect and root out without proper visibility into your environment.
56% of companies have over 500 accounts with passwords that never expire and 44% of companies have more than 1,000 active “ghost user” accounts enabled.
“Manufacturers hold sensitive, and incredibly valuable data that put them at risk. And as we saw with WannaCry, DarkSide and so many other attacks, ransomware can stop production lines and halt businesses. All too often, information is overexposed and under protected. To limit the damage attackers can do, you must reduce your blast radius.
Companies need to ask themselves three questions to better prepare for an attack: Do you know where your important data is stored? Do you know that only the right people have access to it? Do you know that they’re using data correctly? If you don’t know the answers to these three questions, you won’t be able to identity the early stages of a cyberattack,” said Matt Lock, Technical Director at Varonis.
You can read the full report here.