
Dragos has reported a significant rise in industrial ransomware activity in the third quarter of 2025, with new groups emerging, tactics evolving, and major organisations experiencing operational disruption. The company’s latest analysis of ransomware activity affecting industrial environments shows continued escalation across both established and emerging threat actors.
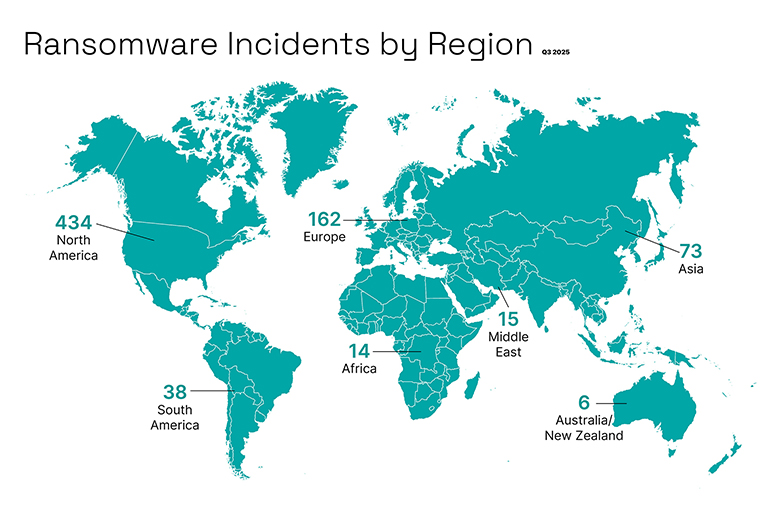
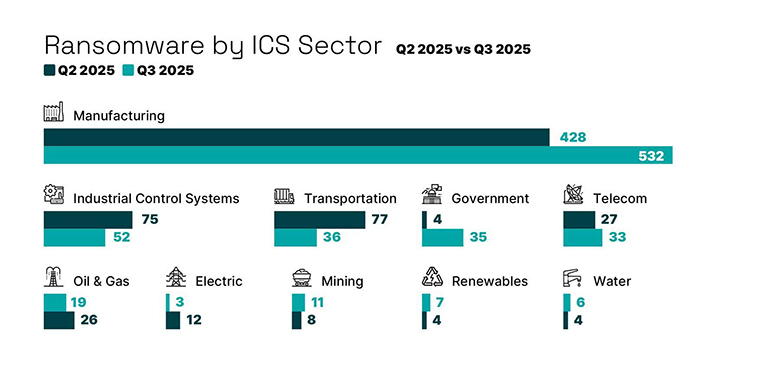
Ransomware attacks impacting industrial organisations increased to 742 in Q3, up from 708 in Q1 and 657 in Q2. Six incidents were recorded in Australia. North America remained the most targeted region, accounting for 434 attacks. Manufacturing continued to bear the brunt globally, representing 72 per cent of all incidents, or 532 cases.
The Qilin ransomware group was the most active for the second consecutive quarter, linked to 138 attacks. Alongside Qilin, Akira, Play and INC Ransom collectively made up nearly 40 per cent of global ransomware activity. Dragos also observed a sharp rise in new and rebranded groups, pointing to growing fragmentation within the ransomware ecosystem. Groups such as Sinobi and Gentlemen heavily targeted industrial organisations, often exploiting compromised credentials and vulnerable VPN services.
A key trend in Q3 was increased adversary focus on IT systems that support operational technology environments. Instead of directly targeting industrial control systems, attackers are compromising enterprise platforms such as ERP systems, virtualisation infrastructure and identity services that are essential to production. Dragos notes that identity-driven tactics, such as those used by Scattered Lapsus$ Hunters, have resulted in significant production shutdowns without requiring direct ICS access.
The quarter also saw several major industrial organisations suffer confirmed operational disruption, including Jaguar Land Rover, Asahi Group Holdings, Collins Aerospace and Data I/O Corporation. These incidents highlight the high-impact nature of ransomware campaigns targeting interconnected industrial and enterprise environments.
Looking ahead, Dragos expects ransomware activity to intensify. Factors driving the anticipated increase include greater ecosystem fragmentation, wider adoption of AI-assisted tools by threat actors and continued targeting of IT systems that underpin operational environments. The company warns that attackers will likely persist in exploiting identity weaknesses, remote access pathways and production-supporting infrastructure to maximise disruption.






