The number of phishing-as-a-service (PhaaS) kits identified in the wild doubled during 2025, underscoring the continued industrialisation of phishing and the growing challenge facing defenders, according to a new threat review from Barracuda.
The analysis found that both new and established phishing kit operators expanded their capabilities over the past year, making advanced attack techniques accessible to a broader pool of cybercriminals. Emerging kits such as Whisper 2FA and GhostFrame introduced more evasive tooling, including techniques designed to prevent analysis of malicious code, while established platforms such as Mamba and Tycoon continued to evolve and remain highly active. Each of these kits was linked to millions of phishing attempts.
Barracuda’s review shows that modern phishing kits increasingly bundle multiple evasion and bypass techniques, reducing the effectiveness of traditional email and web security controls. Multifactor authentication (MFA) bypass techniques were observed in 48 per cent of attacks, matching the prevalence of URL obfuscation methods designed to hide malicious destinations.
CAPTCHA abuse, used to evade automated detection and analysis, featured in 43 per cent of phishing attacks. Around one in five attacks employed polymorphic techniques or malicious QR codes, allowing campaigns to change signatures rapidly or redirect victims through non-traditional vectors. Malicious attachments were present in 18 per cent of attacks, while 10 per cent abused trusted online platforms or leveraged generative AI tools such as zero-code development sites to streamline phishing infrastructure.
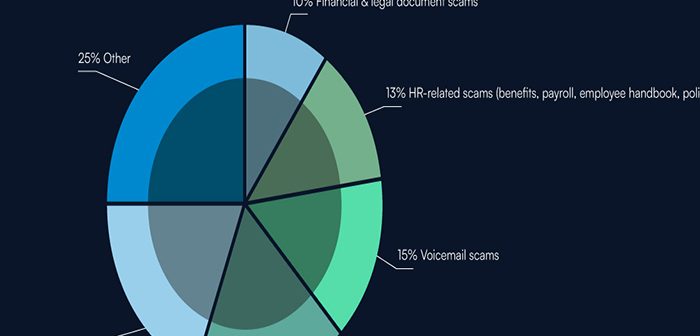
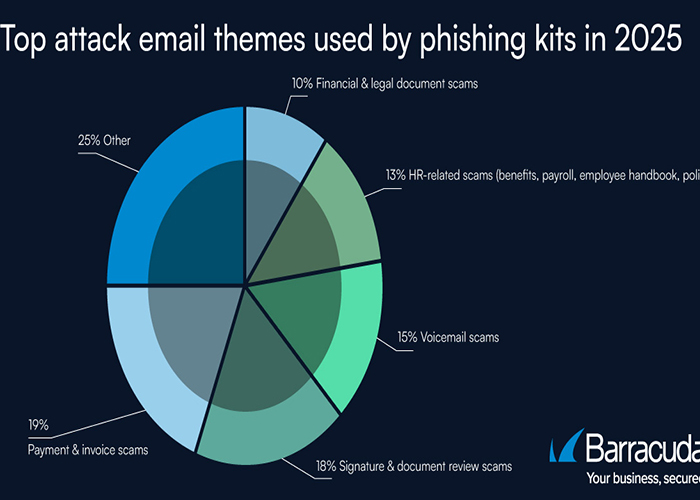
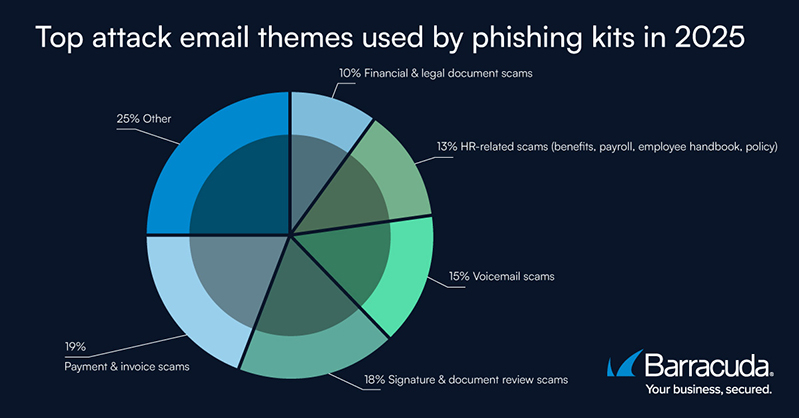
Despite these technical advances, the core social engineering themes used in phishing emails remained familiar. Payment and invoice-related lures accounted for 19 per cent of phishing messages in 2025, while digital signature and document review requests represented 18 per cent. HR-related communications made up 13 per cent of attacks. Barracuda noted that many campaigns exploited well-known brands, with phishing sites and emails increasingly convincing due to the use of generative AI for content creation and visual replication.
Barracuda said the continued growth of phishing kits reflects a shift toward full-service attack platforms, where infrastructure, templates and evasion techniques are packaged together and sold to less-skilled actors. This lowers the barrier to entry while increasing attack volume and complexity.
Ashok Sakthivel, director of software engineering at Barracuda, said phishing kits have become more sophisticated and harder to detect, putting pressure on organisations that rely on static or perimeter-based defences.
“The kits now feature techniques specifically designed to bypass both users and security controls,” Sakthivel said. “As a result, organisations need to look beyond single-layer defences and adopt more resilient approaches that combine user awareness, phishing-resistant authentication, continuous monitoring and integrated email security.”
The findings highlight how phishing remains a dominant initial access vector, even as tactics evolve. While the themes used to lure victims have changed little, the underlying infrastructure and automation supporting phishing campaigns are becoming faster, more adaptive and more difficult to disrupt.