
![]() In the last quarter of 2017, Australian and New Zealand organisations and individuals witnessed a continuation of a trend Proofpoint first observed in 2016 – the disproportionate prevalence of the Ursnif banking Trojan. Ursnif, also known as Gozi-ISFB, is a banking Trojan under continued active development, known for stealthy infection and persistence mechanisms and broad information stealing capabilities ranging from profiles of infected PCs to banking credentials.
In the last quarter of 2017, Australian and New Zealand organisations and individuals witnessed a continuation of a trend Proofpoint first observed in 2016 – the disproportionate prevalence of the Ursnif banking Trojan. Ursnif, also known as Gozi-ISFB, is a banking Trojan under continued active development, known for stealthy infection and persistence mechanisms and broad information stealing capabilities ranging from profiles of infected PCs to banking credentials.
Over the last three months, Proofpoint researchers have observed actors distributing Ursnif in the majority of campaigns identified as targeting Australian users. While Proofpoint can only speculate as to why Ursnif appears more frequently in campaigns than other malware strains, banking Trojans must necessarily be configured for specific banks, businesses, etc., with web injects targeting users of these organisations. Proofpoint often sees a particular affiliate ID of a banking Trojan repeatedly used in one region so that threat actors can maximise the returns on their development time and avoid reconfiguration for organisations in other regions.
In addition to the use of web injects configured for Australian financial institutions, these Ursnif campaigns featured lures with stolen branding and organisation names easily recognised by Australians. Figure 1 shows a lure email purportedly sent by Xero software, a New Zealand-based software company that develops cloud-based accounting software for small and medium-sized businesses.
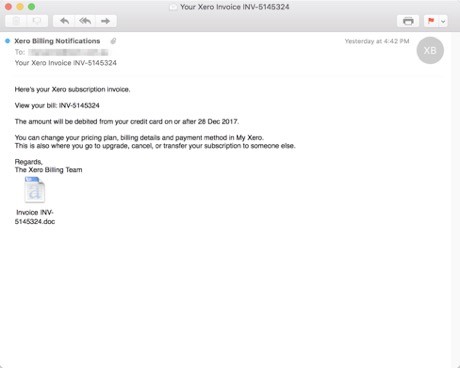
“Figure 1 – A lure email sent by Xero software”
In another case, emails appeared to come from Tax Store Australia, a network of accounting firms and taxation professionals. As with most phishing and malicious spam lures, the brands themselves were uninvolved in the attacks but were simply chosen by the threat actors as recognisable and compelling brands for use in their attacks.
Many of these campaigns were sent by a financially motivated actor Proofpoint refers to as TA543 (aka Sagrid), who frequently abuses legitimate email services like Sendgrid, Constant Contact, and Mailchimp to send malicious spam at scale. TA543 has also frequently abused Microsoft SharePoint to host malware, although recent Microsoft security upgrades to SharePoint are limiting the ability of actors like TA543 to abuse the service.
While Ursnif appears to be a malware of choice for actors targeting Australian users over the last quarter, ransomware and other banking Trojans also appeared in a number of campaigns. Proofpoint also observed broad, multi-regional attacks including Locky ransomware and The Trick banking Trojan affecting Australia while actors less frequently distributed other credential stealing malware like CoreBot and Zloader in the region.
Of note were two interesting multi-faceted campaigns targeting Australia, among other regions. The campaigns attempted to install ZLoader (Windows-targeting banking malware based on Zeus) and an Android banking malware variant in the same email.
CoreBot, on the other hand, has not reached the prevalence of other banking Trojans like The Trick or Dridex. However, it remains under active development and includes sophisticated information stealing and man-in-the-middle attack capabilities. Proofpoint observed several CoreBot campaigns with injects for Australian financial institutions in Q4 2017.
Threat actors tend to follow the money, so if more lucrative options become available, it is likely that they will look to other malware strains. For now, they appear to be following a pattern Proofpoint has observed in other regions with banking Trojans like Dridex in which actors engage in extended distribution in a region before switching to other types of malware.
Conclusion
Because most attacks originate via email, stopping the attacks at the email gateway is an important part of a layered defense strategy. Protection at the network’s edge should include detection of communication with command and control infrastructure while robust endpoint detection can also improve protection against Ursnif. Finally, end user training to help recognise social engineering and potentially malicious mail can help prevent users from opening documents or clicking links that can lead to infection.






