
Written by Jayant Kripalani.
What is BEC and how serious is this problem?
Business Email Compromise (BEC) are a scam in which skilled and motivated cybercriminals trick unsuspecting executives and employees into making payments or sharing sensitive data with fraudulent accounts.
The FBI Internet Crime Report & the Verizon Data Breach Investigations Report explains the gravity of this problem which is a significant and growing concern in the realm of cybersecurity. It poses a serious threat to businesses of all sizes and industries worldwide. The seriousness of the BEC problem can be understood by looking at a few points:
- Financial Losses: According to the FBI’s Internet Crime Complaint Center (IC3), BEC scams were responsible for over $2.7 billion in losses in 2022 alone. These losses can severely impact an organisation’s financial stability and hinder its operations.
- Wide Range of Targets: BEC scams can target various entities, including large corporations, small businesses, non-profit organisations, and even individuals. Attackers exploit vulnerabilities in email systems, human psychology, and business processes, making it a pervasive problem across industries.
- Evolving Tactics: BEC attackers continually evolve their tactics to stay ahead of security measures. They employ sophisticated techniques such as social engineering, email spoofing, and email account compromise to deceive recipients and bypass traditional security defences. This adaptability makes BEC scams particularly challenging to detect and prevent.
- Reputational Damage: Falling victim to a BEC scam can have severe reputational consequences for organisations. It erodes customer trust, damages brand reputation, and can lead to long-term negative impacts on business relationships. Rebuilding trust and mitigating reputational damage can be a time-consuming and costly process.
- Legal and Regulatory Ramifications: Organisations that fall victim to BEC scams may face legal and regulatory consequences. They may be held responsible for failing to adequately protect sensitive data or for breaching privacy regulations. Additionally, organisations may incur penalties, fines, and potential lawsuits from affected parties.
- Operational Disruption: BEC attacks can cause significant disruption to an organisation’s operations. Financial losses, compromised systems, and compromised vendor relationships can impact business continuity and create operational challenges. Recovering from such attacks often requires substantial resources, time, and effort.
- Global Reach: BEC scams are not limited by geographical boundaries. Attackers can operate from anywhere in the world, targeting organisations and individuals across different countries. This global reach makes it challenging for law enforcement agencies to investigate and apprehend the perpetrators.
Why do they work?
BEC’s work quite like Ransomware attacks, as they both attempt to exploit unauthorized access to an organisation’s network. In the case of BEC’s however, criminals capitalize on gaining access to a user’s inbox and contacts rather than the actual computer itself, and then finding ways to monetize that access.
One approach is through internal targeting, where the attackers leverage a compromised employee’s email account to target their own organisation. By impersonating the compromised user, they attempt to redirect payroll deposits into an account they control, aiming to siphon funds from the organisation.
In another approach, attackers can also focus on targeting partners or external parties by exploiting access to an employee’s email account. By impersonating the legitimate user, they can manipulate payment processes and request updates to payments, including their own bank account details. This allows them to divert funds meant for legitimate recipients into their own pockets.
Unlike Ransomware attacks which are exploiting system vulnerabilities that can be patched or for that matter even prevented using different security controls such as Firewalls, Email Gateways, Endpoint Protection, etc.; BEC aims to exploit human vulnerabilities. For example, our ability to easily trust a seemingly genuine email or SMS by just glancing over its contents. This is why they work given they are notoriously difficult to prevent as they exploit human weakness i.e., the perpetrators using social engineering techniques and impersonation to trick people into acting on the attacker’s behalf.
Five common BEC Scams
- CEO Fraud – Attackers impersonate high-level executives within an organisation to deceive employees into performing fraudulent actions or disclosing sensitive information. The goal of this scam is usually to manipulate the targeted individuals into transferring funds, sharing financial data, or providing access to company systems.
- Lawyer Impersonation – Attackers impersonate a lawyer or legal representative threatening their victims with urgent legal action against them unless a payment is made.
- Data Theft – Attackers obtain Personally Identifiable Information (PII) about high-ranking executives by specifically targeting Human Resources personnel.
- Email Account Compromise – An employee’s email account is hacked (or spoofed) and payment requests made to colleagues and vendors, the money being sent to attacker-controlled accounts.
- Vendor Email Compromise – Attackers impersonate vendors/suppliers requesting payments against a fake invoice, the money being transferred to an attacker-controlled or fraudulent account.
Step-by-step breakdown of how a typical BEC scam works
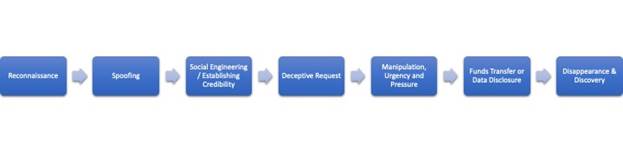
Figure 1 – Breaking down a BEC Scam
Step 1 – Reconnaissance – The attackers research and gather information about the targeted organisation, including the names and positions of top executives, key employees, and their email addresses.
Step 2 – Spoofing – The attackers create deceptive email addresses or domains that closely resemble those of the organisation’s executives or other trusted contacts. They may use techniques like email spoofing or domain impersonation to make their messages appear legitimate.
Step 3 – Social Engineering/Establishing Credibility – The attackers initiate contact with targeted employees, usually those with access to financial or sensitive information, using the fraudulent email address. They might use various tactics to establish credibility and urgency, such as invoking the authority of the CEO or implying time-sensitive business matters.
Step 4 – Deceptive Request – The attackers craft convincing emails that appear to come from a high-ranking executive, often the CEO or CFO. These messages typically request urgent action, such as initiating a wire transfer, making a payment to a specific account, or sharing confidential data.
Step 5 – Manipulation, Urgency and Pressure – The fraudulent emails are designed to manipulate the recipient into bypassing regular security protocols and taking immediate action. Attackers may use psychological techniques, threats of negative consequences, or promises of rewards to convince employees to comply without questioning the authenticity of the request.
Step 6 – Funds Transfer or Data Disclosure – If successful, the targeted employee, believing the email is genuine, transfers funds to the attacker’s account or discloses sensitive information like bank account details, employee records, or trade secrets. In some cases, the attackers may prolong the scam by engaging in further communication to extract additional funds or data.
Step 7 – Disappearance & Discovery – The fraud is often detected after the fact when the legitimate executive or recipient realizes they were impersonated or when financial discrepancies arise. Unfortunately, by this time, the funds may have already been moved to untraceable accounts, making recovery challenging.
Techniques to be aware of
Since BEC relies heavily on Social Engineering, commonly adopted Social Engineering techniques to be aware of:
- Impersonation to exploit “Trust” in Relationships – In the examples above, a successful BEC can unfortunately be attributed to Employees trusting their Employer or Businesses trusting their Vendors. Attackers impersonating Employers or Vendors is common as a result.
- Cloning & Compromising Business Workflows – Emails requesting a password reset, emails pretending to share an attachment, emails from commonly used applications.
- Suspicious Attachments – these might not be picked up by Email Gateways, Anti-Malware or Sandboxing technology since social engineering tactics have been used to create a fake invoice to add to the legitimacy and trap the victim further in believing the perpetrators.
- Socially Engineered Content – email subject lines that have high urgency and want you to act quickly, common words used in BEC subject lines are ‘Overdue’, ‘Immediate Action’, ‘Urgent’.
- Using Free or Low-Cost Technology – email delivery systems for spoofed email addresses, Google Forms and Docs, Box, Google Drive – these are all the tools a clever criminal would need to use to give their BEC scam a sense of legitimacy and socially engineer/exploit human weakness.
Tips to mitigate BEC
Given the seriousness of the BEC problem, organisations must prioritize cybersecurity measures to mitigate the risks. Some tips (not limited to) are –
- Verification Protocols: Establish clear procedures for verifying the authenticity of requests for payments or sharing sensitive information. Implement a multi-step verification process that includes phone calls, in-person meetings; basically, contacting the supposed sender through known, legitimate channels to confirm the request.
- Awareness and Training: Educate employees about the risks of impersonation scams, data theft and provide training on how to identify suspicious emails or requests or phishing attempts. Encourage scepticism when clicking on links, attachments etc. in emails and promote a culture of verifying before taking any action.
- Multi-Factor Authentication (MFA): Implement MFA for user accounts, email accounts and other critical systems to add an extra layer of security, reducing the risk of unauthorized access or account compromise.
- Email Filtering and Anti-Spoofing Measures: Utilize email filtering systems and anti-spoofing technologies to detect and block malicious or spoofed emails. These measures can help identify and flag potentially fraudulent emails.
- Enforce Strong & Unique Passwords: Encourage individuals to use strong, unique passwords for their email and other online accounts, and regularly update them to reduce the risk of unauthorized access.
- Cybersecurity Measures: Deploy robust cybersecurity solutions for example, anti-malware software, and firewalls, to detect and block malicious emails or attachments. If already deployed, then periodically review the architecture, and build a plan to augment or enhance existing technology. As an example, you could augment an existing Email Security Gateways with – technologies that are Context-aware, leverage AI/ML, build SOAR playbooks, use Threat Intel, implement DMARC solutions – to name a few.
- Data Encryption: Implement strong encryption for sensitive data, both at rest and in transit, to mitigate the impact of potential data breaches.
- Incident Response Plan: Develop an incident response plan that outlines the steps to be taken in case of a data breach, BEC or suspected data theft. This plan should include procedures for reporting incidents, notifying affected parties, recovering lost funds (if possible) and mitigating further damage.
- Regular Security Updates: Keep email clients, web browsers, and operating systems up to date with the latest security patches to mitigate vulnerabilities.
- Collaboration: Collaboration between organisations, cybersecurity experts, and law enforcement agencies is also crucial to combatting the BEC problem effectively.
Reference(s):
- FBI Internet Crime Report 2022 (https://www.ic3.gov/Media/PDF/AnnualReport/2022_IC3Report.pdf)
- Verizon Data Breach Investigations Report 2023 (https://www.verizon.com/business/resources/T7b/reports/2023-data-breach-investigations-report-dbir.pdf)
About the Author:
Jayant Kripalani has over 20 years of experience in the Cybersecurity industry working with customers across various industry verticals, while working at some of the largest Security companies such as Rapid7, McAfee, Cisco, and Splunk. He has international experience having lived and worked in the world’s biggest global markets such as New York, Melbourne, Mumbai, and Bangalore. In his adventures working in Cybersecurity, he has built and mentored SOC teams, led SOC teams with people from diverse cultural backgrounds and varied technology skill sets. He holds a bachelor’s degree in Computer Engineering in addition to multiple industry certifications.






