Group-IB has issued a comprehensive report on Fxmsp – a heavyweight of the Russian-speaking cyber underground who made a name for himself selling access to corporate networks. Group-IB researchers analyzed Fxmsp’s activity on underground forums for about three years and discovered that the threat actor had compromised networks of more than 130 targets, including SMEs, government organizations, banks, and Fortune 500 companies all around the world. The report shows how Fxmsp’s cybercriminal career evolved from a newbie hacker to one of the major players of the Russian-speaking underground. Group-IB’s team uncovered Fxmsp’s TTPs and established his presumed identity. Despite the fact that Fxmsp has ceased all public activity, it’s not unlikely that he continues to attack corporate networks and sell access to them. Given these risks, Group-IB decided to release the report “Fxmsp: ‘The Invisible God of Networks,’” share its expanded version with international law enforcement agencies, and make its materials on Fxmsp’s tools and tactics accessible to the general public.
Geography and victims
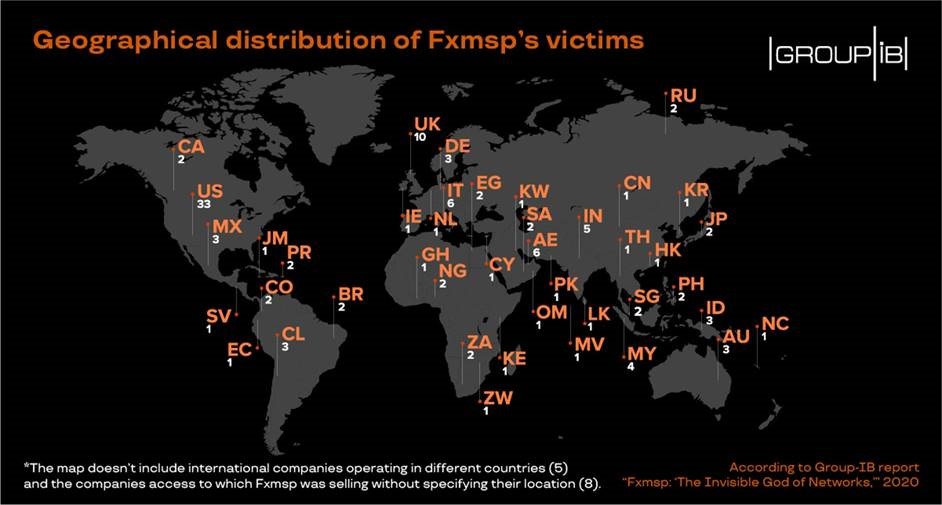
Fxmsp gained worldwide fame in May 2019, after it was reported that the networks belonging to leading antivirus software companies had been compromised. However, no one knew until now the story behind this unusual nickname and the sheer volume of the crimes committed. In just about three years, Fxmsp managed to gain access to corporate networks of 135 companies in 44 countries, including in the US, Russia, Singapore, the UK, and elsewhere.
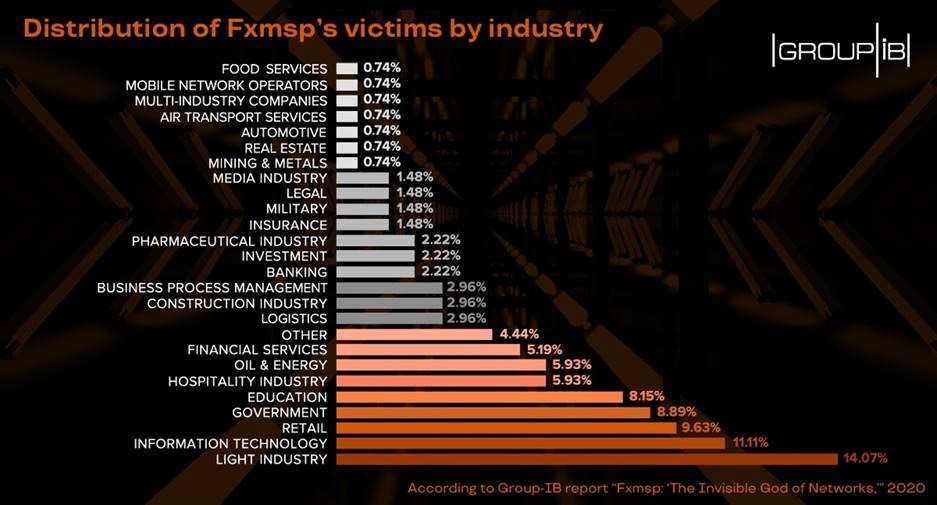
According to Group-IB researchers’ conservative estimates, Fxmsp and his accomplice are likely to have made at least $1.5 million throughout their operations. This, however, does not include the 20% of companies to which he offered access without naming the price and the sales he made through private messages. His actual earnings are believed to be much higher. Fxmsp’s victims were mainly companies in the light industry, i.e. focused on small production of consumer goods. His second most favorite targets were companies offering IT services. It’s of particular note that around 9% of victim networks belonged to government organizations, while four companies successfully attacked by the threat actor were included in the Fortune Global 500 ranking in 2019. It’s worth noting that despite the fact that Fxmsp stopped all public activity in late 2019, Group-IB discovered that a European energy company, that he was selling access to, fell victim to a ransomware attack in 2020.
Group-IB’s attribution-based Threat Intelligence system makes it possible to monitor all posts on underground forums in real-time and gain access to both original posts and all edit history. Therefore, the company’s researchers were able to retrieve and analyze hundreds of Fxmsp’s posts, including the ones he had deleted and edited, which allowed to look into the history of his crimes, the evolution of his character, and establish the exact methods he used to compromise corporate networks.
First steps
Fxmsp took his first steps in the cybercrime scene in September 2016 when he registered on an underground forum, fuckav[.]ru. His early posts indicate that Fxmsp had little knowledge about how to monetize the access and maintain persistence within the networks he had compromised. He was asking around about self-propagating persistent cryptomining malware and other Trojans for infecting corporate networks seeking for help with accesses he had gained, making a number of mistakes along the way. Experienced users of underground forums never publish their contact details, they share them only through private messages. Fxmsp included one of his Jabber accounts, in his contact information on the forum which helped Group-IB researchers to establish his presumed identity.
In early 2017, he created accounts on several other Russian-speaking forums, including on the infamous exploit[.]in, where he refocused his activity and began selling access to compromised corporate networks which would later become his primary business. On October 1, 2017, Fxmsp published his first ad for the sale of access to corporate networks. His first victim in the financial industry was a commercial bank in Nigeria. Later, he would announce the sale of access to the network belonging to a chain of luxury hotels, another African bank with a capitalization of $20 billion, and many other high-profile targets.
First falls
Fxmsp learned very fast with help from other forum members. Soon enough, the threat actor started talking about hacking into IBM and Microsoft. Puffed up by his initial success, he forgot an unspoken rule in the Russian-speaking hacking community: not hacking within Russia and CIS countries. Fxmsp tried to sell access in Russia and was eventually banned from the forum. The hacker learned his lesson. He deleted all offers linked to Russia and the ban was lifted. Nevertheless, Group-IB Threat Intelligence team was able to retrieve his deleted posts and discovered that in December 2017 Fxmsp had published an ad for the sale of access to an ATM and to the website of the customs office in two Russian cities.
Proxy seller
On January 17, 2018, the hacker shared exactly how many buyers he had at the time: 18. The business was going so well for Fxmsp that he hired a user with a nickname Lampeduza (aka Antony Moricone, BigPetya, Fivelife, Nikolay, tor.ter, andropov, and Gromyko) as his sales manager in early 2018. Lampeduza began sharing posts about the sale of access to the very same companies that Fxmsp had mentioned earlier. Promoting their services, Lampeduza wrote in one of his forum posts “…You will have access to the company’s entire network … You will become THE INVISIBLE GOD OF NETWORKS…” During their cooperation, the two advertised the sale of access to 62 new companies. The total price for all the access sold was $1,100,800.
In late October 2018, Fxmsp and Lampeduza’s activity became threatened. It turned out that they were trying to sell access to the same network to several different buyers. The clique temporarily suspended its activity on all other forums and allegedly focused on “private sales,” i.e. they started working only with a limited circle of clients. In mid-March 2019, the co-conspirators resumed their activity on forums. New messages about the sale of access appeared on several underground message boards.
The big fish
Fxmsp’s public activity culminated in April 2019. According to media reports, Fxmsp had managed to compromise networks belonging to three antivirus software vendors. Following the incident that hit the headlines, in May 2019, Lampeduza stated that he no longer worked with Fxmsp, denied any involvement in the high-profile hack, and said that he had allegedly suspended their cooperation on underground forums due to the greater media attention to Fxmsp. Thereafter, Lampeduza once again disappeared from forums for a while, but most likely continued selling accesses provided by Fxmsp through private messages to regular customers. On December 17, 2019, Lampeduza confirmed to the forum users that Fxmsp had stopped his activity.
“Fxmsp is one of the most prolific sellers of access to corporate networks in the history of Russian-speaking cybercriminal underground who publicly advertised the access to 135 companies, which brought him more USD 1.5 mln in profits,” comments Dmitry Volkov, CTO of Group-IB. “He set a trend and his success inspired many others to follow suit: the number of sellers of access to corporate networks increased by 92% in H2 2019 vs H1 2017, when Fxmsp entered the market. Prior to Fxmsp joining the underground, the sellers would offer RDP access to separate servers, without even bothering to ensure persistence or performing reconnaissance in the network. Fxmsp took this service into a whole new level. Despite rather simplistic methods he used, Fxmsp managed to gain access to energy companies, government organizations and even some Fortune 500 firms. Fxmsp had indeed ended all public operations, however, it’s not unlikely that he continues making private offers posing a threat to companies in many industries, regardless of their location. In light of this, we decided to release this report, make our materials on Fxmsp’s TTPs accessible to the public, and provide recommendations to help companies protect against the types of attacks conducted by Fxmsp and similar cybercriminals. We hope that our research will help to locate and arrest the threat actor hiding behind the nickname Fxmsp and his accomplices, which is why we’ve shared the expanded version of the report with international law enforcement agencies.”
TTPs
The digital traces Fxmsp left at the earliest stage of his career, allowed Group-IB Threat Intelligence team to establish his toolset and methods. In most cases, Fxmsp uses a very simple, yet effective approach. He scans a range of IP addresses for certain open ports to identify open RDP (remote desktop protocol) ports, particularly 3389. Then, he carries out brute-force attacks on the victim’s server to guess the RDP password. After gaining access to the target device, Fxmsp usually disables the existing antivirus software and firewall, then creates additional accounts. Next, he uses the Meterpreter payload on servers as a backdoor. Fxmsp himself noted in his posts that, when installing backdoors, he set a long interval for connections with C&C servers: once every 15 days. Once the access is gained, Fxmsp harvests dumps of all the accounts and decrypts them. Finally, he infects the backups by installing backdoors. Even if the victim notices suspicious activity in the system, they will most likely change passwords and perform a rollback to the backup, which has already been compromised. This approach allows him to maintain persistence and remain unnoticed for a long time.
Recommendations
At the time of writing, Fxmsp is no longer conducting public activities. It is uncertain, however, whether he is still breaking into company networks and continues to make private offers. Given the risks, we deem it essential to offer universal recommendations on how to prevent attacks that bear similarities to those conducted by Fxmsp.
Fxmsp uses open RDP ports as the initial attack vector, therefore, the default RDP port 3389 can be edited by changing it to any other. As the attackers usually need several attempts to brute force passwords and gain access to the RDP, it is important to enable account lockout policies by limiting the number of failed login attempts per user. Another important element to ensure resilience against this type of attack is to constantly monitor the darknet for compromised data related to your company. Threat intelligence solutions enable organizations to mitigate risks and further damage by quickly identifying stolen records and track down the source of the breach, while specialized threat detection systems allow to discover unwanted intrusions, traffic anomalies within the corporate network, and attempts to gain unauthorized access to any data.