The recent hack of the MGM casino in Vegas put ransomware gangs’ interaction with the media in the spotlight, with Black Cat publicly calling out reporters for “inaccurately” attributing the hack to Scattered Spider.
After taking a closer look at the dark web and ransomware leak sites, Sophos X-Ops has uncovered that this was not a one-off: ransomware groups are increasingly turning to the media to increase their notoriety and pressure on victims to pay.
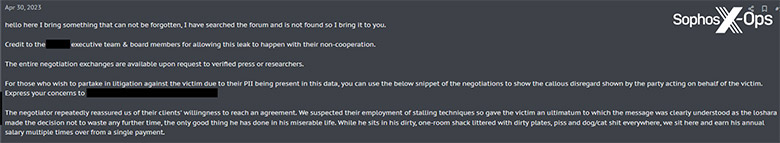
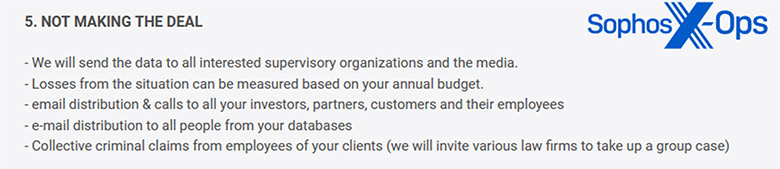
Sophos X-Ops found multiple posts on criminal forums and leak sites from threat actors that included threats to reveal a company’s data breach to the press. They’ve also uncovered similar threats in ransomware notes left by Royal and Inc during their own in-the-field investigations.
 Ransomware groups are utilising a range of strategies to maintain direct lines with the media. On ransomware leak sites, Sophos X-Ops found special Telegram channels and contact forms for press, FAQs for media, and special offers of “collaboration” with journalists. By engaging with the press and earning credit for attacks, ransomware groups can increase their notoriety, which, in turn, can improve their recruitment efforts. Sophos X-Ops even found ads for English language writers on criminal forums, possibly to write copy for leak site “blogs” that publicize the groups’ attacks and highlight articles by mainstream press in which they are featured.
Ransomware groups are utilising a range of strategies to maintain direct lines with the media. On ransomware leak sites, Sophos X-Ops found special Telegram channels and contact forms for press, FAQs for media, and special offers of “collaboration” with journalists. By engaging with the press and earning credit for attacks, ransomware groups can increase their notoriety, which, in turn, can improve their recruitment efforts. Sophos X-Ops even found ads for English language writers on criminal forums, possibly to write copy for leak site “blogs” that publicize the groups’ attacks and highlight articles by mainstream press in which they are featured.
 Christopher Budd, director, threat research, Sophos said, “Ransomware attackers are no longer simply hacking networks and systems—they’re attempting to ‘hack’ the public narrative. We saw this with the MGM hack, and even with the MOVEit attacks by Cl0P, when the group attempted to ‘set the record straight’ about purported inaccuracies in the media’s coverage of the attacks. For these threat groups, there’s several benefits to engaging with the press. It’s not only an ego boost for them but improves their notoriety—and makes them a more desirable ‘employer’ for criminals. It’s also shown to be an effective method for pressuring victims. We’re likely to see ransomware groups more directly engaging with the press in the future. In our research, interestingly enough, we saw some groups like Cl0P and Royal utilising press releases to ‘rebrand’ their activities into ‘security services’. We’re not sure why; it could be a recruitment tactic or an attempt to improve their public image. Regardless, it demonstrates these threat groups’ concerted effort to shape public perception. For defenders, it’s important not to give in to their desire for attention. We need to focus on the tactics, techniques, and procedures (TTPs) of the attacks, so we can bolster companies’ defenses, rather than ‘who’ was behind the attack.”
Christopher Budd, director, threat research, Sophos said, “Ransomware attackers are no longer simply hacking networks and systems—they’re attempting to ‘hack’ the public narrative. We saw this with the MGM hack, and even with the MOVEit attacks by Cl0P, when the group attempted to ‘set the record straight’ about purported inaccuracies in the media’s coverage of the attacks. For these threat groups, there’s several benefits to engaging with the press. It’s not only an ego boost for them but improves their notoriety—and makes them a more desirable ‘employer’ for criminals. It’s also shown to be an effective method for pressuring victims. We’re likely to see ransomware groups more directly engaging with the press in the future. In our research, interestingly enough, we saw some groups like Cl0P and Royal utilising press releases to ‘rebrand’ their activities into ‘security services’. We’re not sure why; it could be a recruitment tactic or an attempt to improve their public image. Regardless, it demonstrates these threat groups’ concerted effort to shape public perception. For defenders, it’s important not to give in to their desire for attention. We need to focus on the tactics, techniques, and procedures (TTPs) of the attacks, so we can bolster companies’ defenses, rather than ‘who’ was behind the attack.”