Tenable has released an Exposure Management platform, Tenable One, that unifies discovery and visibility into all assets and assesses their exposures and vulnerabilities across the entire attack surface for proactive risk management.
At launch, Tenable One introduces three new capabilities that are foundational to exposure management programs:
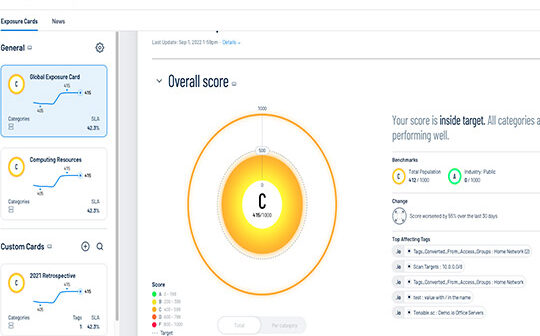
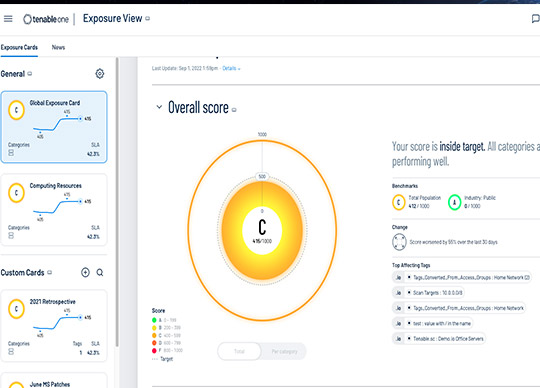
- Lumin Exposure View – provides clear and concise insights into an organisation’s cyber exposure, giving security teams the ability to surface and accurately answer critical questions about security posture
- Attack Path Analysis (APA) – enables security teams to view attack paths from externally identified points through to critical internal assets to focus mitigation on areas of highest risk
- Asset Inventory – provides users with a centralized view of all assets, including IT, cloud, Active Directory and Web applications, with the ability to create specific asset tags from a variety of sources and use cases
“Bad actors don’t take a siloed approach to exploiting organisations’ attack surfaces, so why are cybersecurity teams operating in vacuums?” said Glen Pendley, Chief Technology Officer, Tenable. “A platform approach to exposure management is the real game changer, surpassing the ineffective and expensive point solution approach that the industry has taken for decades. Tenable One delivers holistic insight into exposures that can serve as a true north for security teams.”
Tenable One combines vulnerability management, external attack surface management (EASM), identity management and cloud security data to discover weaknesses before attackers can exploit them. It continuously monitors environments – from traditional IT assets to cloud resources and identity systems – delivering the broadest vulnerability coverage available.
Tenable One enables organisations to:
Visualise Assets and Vulnerabilities – eliminates areas of known and unknown security risk and builds a baseline for effective risk management. It combines the power of a unified view of all assets and associated software vulnerabilities, poor configurations and excessive entitlements with continuous vulnerability assessment.
Predict and Prioritise – applies context to anticipate the consequences of a cyberattack faster and significantly improves remediation prioritisation. It enables security teams to continuously identify and focus on the exploitable attack pathways that create the most risk.
Effectively Communicate Risk – provides a centralised and business-aligned view of cyber risk and actionable insights. It enables organisations to accurately and effectively communicate to different stakeholders about cyber risk and which actions can most efficiently reduce it.