Insights interview with Tammy Schuring, Vice President of Sales, Hewlett Packard Enterprise
When discussing the focus for data security at Hewlett Packard Enterprise (‘HPE’), it becomes apparent that the worldwide news and headlines of cyber-attacks over recent years, remains a prime motivator for treating the risk of a data breach. Based in Silicon Valley, Tammy Schuring, Vice President of Sales for HPE Security – Data Security, came into the role in 2015, having dedicated over a decade to growing a loyal customer base. Tammy continues to evangelise a fundamental security approach, protect ‘the data’.
 Tammy was in Australia meeting with customers to provide her own insights into the capability of monetising data—be it personally identifiable information, healthcare, financial or similar sensitive information. Tammy asserts, “unfortunately, companies the world-over are faced everyday with the daunting realisation that it’s not a matter of ‘if ’ they are breached, it’s a matter, ‘are’ they being breached now, have they ‘already’ been breached or are they ‘about’ to be breached. It’s a change in mindset. Whether it’s an insider threat, or a cybercrime organisation that’s patiently looking for a way to get in or that is already syphoning off data. It’s stepping out and saying at the outset: it’s not a matter of whether we can keep them out, we need to start seeing through the lens of its already happening.”
Tammy was in Australia meeting with customers to provide her own insights into the capability of monetising data—be it personally identifiable information, healthcare, financial or similar sensitive information. Tammy asserts, “unfortunately, companies the world-over are faced everyday with the daunting realisation that it’s not a matter of ‘if ’ they are breached, it’s a matter, ‘are’ they being breached now, have they ‘already’ been breached or are they ‘about’ to be breached. It’s a change in mindset. Whether it’s an insider threat, or a cybercrime organisation that’s patiently looking for a way to get in or that is already syphoning off data. It’s stepping out and saying at the outset: it’s not a matter of whether we can keep them out, we need to start seeing through the lens of its already happening.”
INOCULATING SENSITIVE DATA
HPE is attacking the data protection problem right at the heart of a much-needed solution. Tammy explains, What we do at Data Security inside HPE is inoculate sensitive data, so when it’s in the wrong hands, it cannot be used against the customer, be it a company or person. The ability to take sensitive data that the cyber criminals can use, to create money, be it a fraudulent tax return, or credit information, and protect it yet have the data retain its format and its logic inside the company, is huge. This way, if the protected data gets stolen, it cannot be monetised. It cannot be used somewhere else – it’s not actually the real data.”
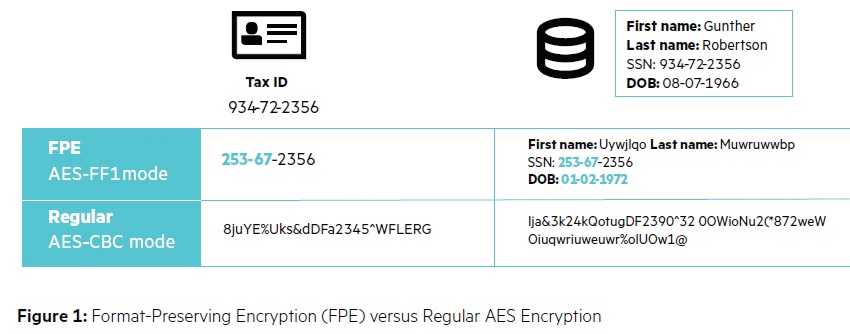
Typically, when encryption or tokenisation is applied, it transforms the data into an unusable, very long string—be it a 256-bit or 128-bit string; and applications cannot function with de-identified data. HPE SecureData has enhanced the cryptology in such a way that when the data is de-identified, what comes out the other side retains that expected format. It retains the logic, as a random set of numbers or letters would otherwise not present. For example, HPE’s Secure Data will pass Checksum, in the case of PAN (primary account number) data.
“The other key element,” Tammy highlights, “is it can also retain data relationships, with what in technology is
called, ‘referential integrity’. By preserving the referential integrity—your relationship to your address, phone number, your credit card data, your account number, your health data—all of those relationships are preserved, even when we are encrypting or tokenising those elements. Metadata can also be preserved, and that’s an aspect of its logic. The ability to retain as much of the principals of the data. Companies can start to operate on the de-identified data and you will find companies typically have 50 and up to 120 data types that are viewed to be sensitive data.”
“We’re taking the threat surface and drastically reducing it.” As an analogy, Tammy commonly likes to use, “it is gold versus fool’s gold – we are figuratively transforming the gold into fool’s gold. It looks like gold, it acts like gold. The data ‘shimmers’ throughout the system; but when the bad
guys steal it, they spend a lot of money and time trying to monetise it and they simply can’t—because it’s not real data, but it absolutely looks like data.”
ABILITY TO DECIDE ON SECURITY
HPE SecureData has built a loyal customer base across a wide range of industries, with the standards-based
technologies of HPE Format-Preserving Encryption (FPE) and HPE Secure Stateless Tokenization (SST).
HPE FPE is an encryption technology that preserves the original data format in the encrypted state, as well as context value, relationships and meaning, enabling business process and secure analytics.
HPE SST provides advanced data security without token databases. HPE SST improves speed, scalability, security, and manageability over conventional and first-generation tokenization solutions. These technologies protect the data, and the protection is carried with the data itself – wherever it goes – in-motion, at-rest, and while in-use.
Tammy described how customers have the ability to decide, from a rules perspective, how they want the deidentified data to appear, either once it’s been encrypted or decrypted, she said, “One of the things customers can do is called ‘obviously protected’. They can choose to transform it, perhaps as an example, add letters and visually see that this is in fact not the real data, so there are ways to decide, for a particular attribute of the use case or bi-product of the system.”
PSEUDONYMIZATION MEETS GDPR
There are a number of regulations that companies must comply with, such as PCI DSS (Payment Card Industry Data Security Standard) through to the emerging regulation of GDPR (General Data Protection Regulation), and a wide range beyond that. Tammy notes, “At the end of the day, interestingly, regulations and audit compliance may be only pointers in the right direction. Just ask any compliant company that has still experienced a data security breach.” Tammy assured, saying, “If anybody believes that compliance equals security, just go read the news any day of the week. Customers are able to leverage our solution to greatly reduce their compliance scope and save personnel hours, and that’s not even the best part of the story.”
“The best part of the story,” Tammy says, “is where they end up at the other side. It is truly addressing the risk. The risk that even if you were compliant, and have reduced the compliance footprint, like we do with PCI so dramatically, and you still suffer a breach. If that data is stolen, that data itself cannot be monetised. The ability to leverage the format preserving encryption and format preserving tokenisation, that we bring to the market, enables them to protect the data at capture and keep it protected throughout its lifecycle. There’s no longer a need to decrypt it to determine where it goes next. It ends up staying in its protected state.”
GDPR will greatly impact how companies will deal with data, going beyond just fines and protecting personal information, but opening avenues to a world of lawsuits and empowering the individual to take action. Up to four percent of a company’s annual turnover (Article 83, GDPR) is potentially at risk, so the stakes are tremendously high.
Tammy explained, “There are specific aspects within GDPR that deal with data protection, and I am talking about pseudonymization. If you leverage this, to a great extent, it is almost the “get out of jail free” card.” Tammy said, “If you are taking this personally identifiable information as defined by GDPR, and you’re leveraging a data protection solution such as HPE SecureData, you’re keeping all the benefits of the data but you’re leveraging pseudonymization. Such that, should something happen to the data, and it is lost or stolen, the data is useless to the attackers, and is therefore a nonevent and that is the ideal scenario.”
BIG DATA INNOVATIONS
One of the big innovations is around data itself. Tammy notes, “If you go back just a few years, the amount of data that we could consume and do real-time analytics on pales in comparison to what we can do today. There is so much value in being able to take not only the data a company has, but bringing in data from other sources. Working with some of the car manufacturers and their belief there should never be a recall on a car again, because these cars are so instrumented and with so much data coming out of them, they should get ahead of any problem that would come up. But it wasn’t until ‘big data’ that they could see the patterns light-up in real time, in order to determine where they needed to make adjustments. Once they figured out with these innovations in technology, there was a major inhibitor standing in their way – and that was security.”
“The proposition was there, but how could you take so much sensitive data about just one person? Their personally identifiable information, the vehicles’s identification number or VIN, where they’re going, GPS data, how fast they’re driving, you name it. How many times are they are hitting the breaks, and to put that essentially into a huge soup pot that’s based on Hadoop, innately probably the most insecure platform on the planet right now. The risk was too high.”
“What we’ve been able to do with the SecureData technology is apply it into the world of big data analytics. For
example, with the car manufacturers, that ability to protect the data in a way that the format is preserved, the logic is preserved, and most importantly the relationships. It is not important to know all the individual pieces of information and details. What is important is ability to detect the patterns. There is so much data there, the problem really isn’t an ability to associate with one particular person, but the ability to see those patterns.”
WAVES STARTING TO HIT: ACCESS TO THE CLOUD & INTERNET OF THINGS
Tammy highlights, “One of the key aspects that is shining a light on this technology’s evolution is access to the cloud. The ability to embrace public cloud can save companies a tremendous amount of money by giving them access to things that they didn’t have access to before.” Referring to a large car brand as a customer, Tammy said, “they discovered they can save 40 per cent, per application, per year, if they moved their .NET applications to Microsoft Azure. This value proposition is potentially tens of millions, if not hundreds of millions of dollars in some cases, over a five-year period. When this was realised in one of the business units, the CEO
was naturally very excited with such an innovative, costsaving measure. Before proceeding, Security asked one simple question—is there any sensitive data, including PAN data, involved? The answer was, ‘yes’. Yet before objecting to the project, someone on the CISO’s team had recalled our ability to secure the data and preserve the format. Without creating a bigger processing footprint in putting this data into the cloud, in these .NET applications, the concerns the customer had around the data were addressed. The applications did not
have to change their data model. With the data format and data relationship integrity staying intact, there was no need for any rule changes.”
“We match the elasticity model in the underlying platform,” Tammy continued, “so most of our customers decide they want this data-centric protection model across their entire organisation. They don’t want to have to decide if it will only be in the Hadoop environment, or only in their mainframe, or .NET, or J2EE (Java Platform Enterprise Edition) applications, or open system applications. What we do is match to the acuity model of that environment. Such as in Hadoop, that is a node-based environment and we can sell our product based on the node count; for a smaller organisation with 10-20 nodes, through to some of the largest customers in the world, with tens of thousands of nodes, we have a model that can be adapted for all.”
IoT is an exciting paradigm and the wave is just starting to hit. However, Tammy asserts, “there is so much data and this can be used very maliciously. Be it a driverless car or a medical device, should someone manipulate that, the impact is no longer how much data can I monetise, the impact is on people’s lives.”
The HPE SecureData technology comes packaged as either an API (Application Programming Interface) or an
SDK (software development kit). HPE has a mobile SDK which allows companies to build right into their mobile
applications. The capture of data and format preserving encryption paradigm, as we’re all out on the go, entering various information into our devices, right at capture, can be protected. Tammy explained, “It’s not sitting in memory in clear text. The vulnerability aspect of what these mobile devices bring is addressed. We’re seeing with IoT, the power, scale, innovation, is exponentially improving, not in years now but in months. What could be done a year ago, pales in comparison to what will be done a year from now. The ability to build in this
encryption, right at capture from inside these IoT devices, is there in many cases, or on the verge of being there.”
“When you look at the difference in the innovation, in regards to encrypting and keeping the format the same, versus bloating it into a 256-bit string, that impact is minimal. We’ve been deployed with two of the biggest card brands in the world, with every single card transaction related to them. The ability to be in every single transaction means it has to meet requirements in performance and scale. SecureData has the ability to take any production data, like transaction information, be it per second information, latency information, and then turn it around and apply it in the world’s top financial institutions, healthcare and retailers. We can show
that at scale, so the customer’s requirements are often so much lower than we’re already being applied to.”
“One of the key elements of what powers a lot of what HPE SecureData does and why this is being adopted so
broadly now, is that the technology has format preserving encryption, now a mode of AES (Advanced Encryption Standard). We have received our NIST (National Institute of Standards and Technology) certification as FFX1, and our FPE technology provides accelerated encryption performance up to 170 per cent in conservative scenarios. Building on today’s proven high-speed FPE technology, while aligning to the high-volume needs of next generation Big Data, cloud, and IoT scenarios. With the power of what this algorithm
can do in terms of enhancing the encryption footprint, the US Federal Government fast-tracked it to make it a standard and now, as we’re finalising our FIPS 140-2 and Common Criteria, this opens up many areas. Where it was already being leveraged before that certification, it is now able to be used by government entities and other entities who set the bar and this standard is a requirement.”
CAPTIVATING AUSTRALIA
“Australia is a very interesting market,” Tammy observes, “we started investing here about seven years ago and have a lot of interest. One of the main discussions back then was PCI (payment card industry) and companies wanting to get to compliance – there wasn’t the view that there was the same kind of risk as there was in other parts of the world.”
“Paradigms like big data, cloud, mobility and with data so transient now, the Australian market is much more exposed, and a light has been shone on it. Big data is probably the biggest driver now, and regulations like GDPR are right behind it, as well as the drive to public cloud.”
The Australian market has a tremendous need, Tammy notes, “I spent time with the Government and large financial services, elecommunications, retailers, sports betting—and I was shocked. I was last in Australia, literally at the time when the Census breach was happening, and seeing the way that sensitive information is being used in this country. I found having been an evangelist of this approach across the globe, it has really surprised me how often a national ID, or a credit card number or an account number is used as a primary key and mode of identification. There is a lot of ground to cover here.”
Tammy concludes, “I think the Census example, of showing how systems can fundamentally break down, showed when the confidence of the citizens in those systems evaporates. So, having returned to Australia this year, there is such a desire now to protect the information and it’s no longer about meeting a particular regulation as the driver, be it PCI or GDPR – it’s really about the overarching sense of confidence and protection of brand.”